-
A Bookmarklet to Download Zoom Recordings
I share a simple bookmarklet that downloads recorded Zoom videos from the Zoom cloud.
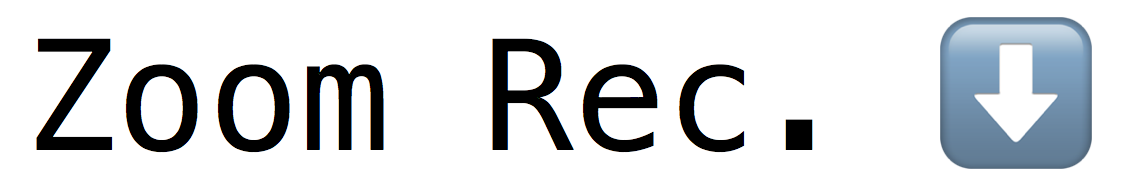
-
Hash Functions are not (Quantum) Random Oracles, but only Technically
In this post, we define the Random Oracle Model (ROM) and the Quantum ROM (QROM), and give some examples of their uses and their flaws. We show that the QROM is unsound in the same way that the ROM is, and we conclude that that's OK.
-
Supersingular Isogeny Key Exchange for Not-Quite Beginners
I recently read a great introductory paper on Supersingular Isogeny Diffie-Hellman (SIDH) by Craig Costello and wanted to summarize just the math of it (with some simplifications) for myself. Hopefully this summary is clear enough to also be useful to people who aren't myself.
-
Better Encrypted Group Chat
Making end-to-end encrypted group chat both efficient and secure is difficult. In this article, I explain why it's so difficult and present a new protocol that attempts to solve this problem.
-
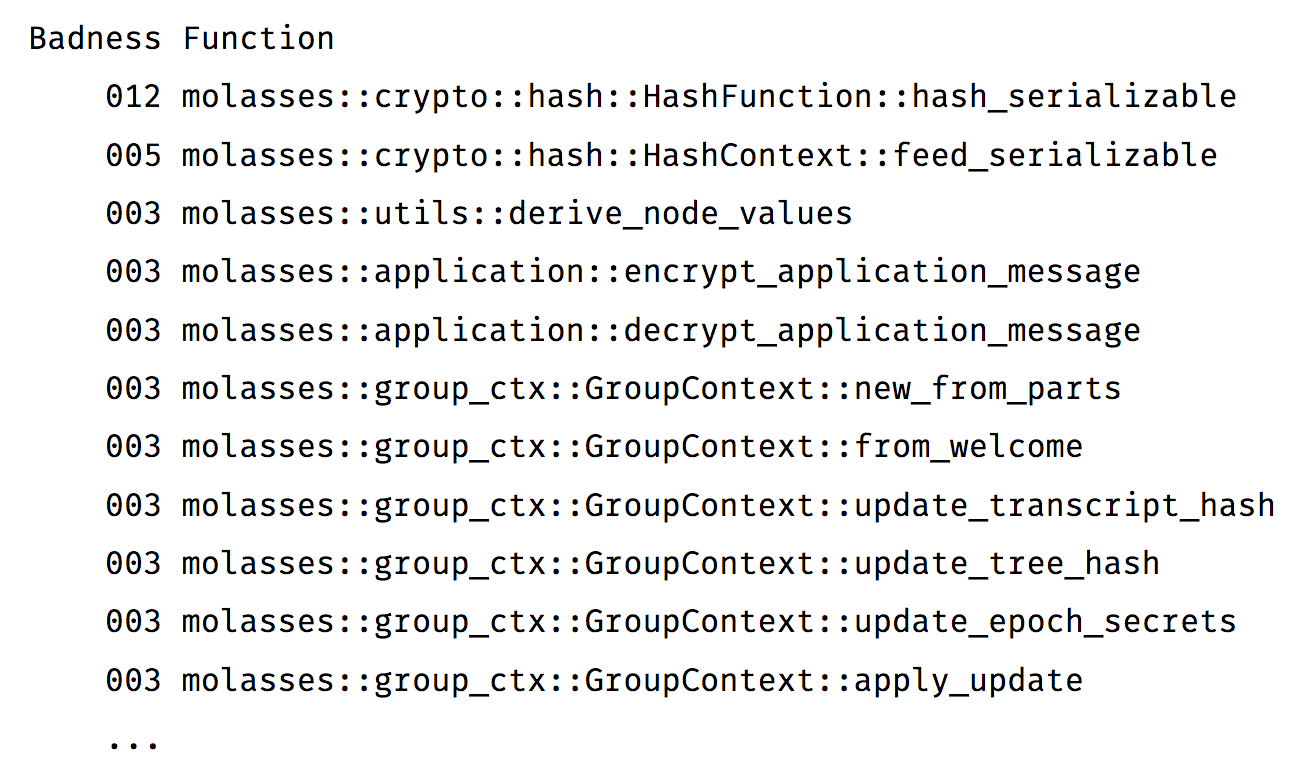
Siderophile: Expose your Crate's Unsafety
This marks the release of `siderophile`—a tool for quantifying the unsafety of all the functions, expressions, methods, etc. in your Rust crate.
-
Confidential Transactions from Cryptographic Primitives
Bitcoin today publicly reveals how much Bitcoin is sent in every transaction. Some cryptocurrencies wish to make these values private by default, but this comes with some mathematical challenges. We explain here what it takes to construct confidential transactions, assuming a basic background in cryptography and algebra.